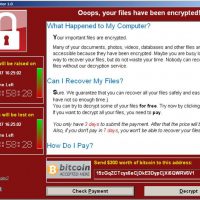
Penetration Testing RFPs – Tips and Tricks
Penetration testing requests for proposals (RFPs) or requests for quotes (RFQs) can be a great way to bid on and potentially win penetration testing projects as a business. Many pen testing vendors rely on capturing business solely, or mostly, through RFP submissions. Most RFPs are for government entities such as local municipalities, state run schools, […]