AWS S3 SSE-C Today, Gone Tomorrow
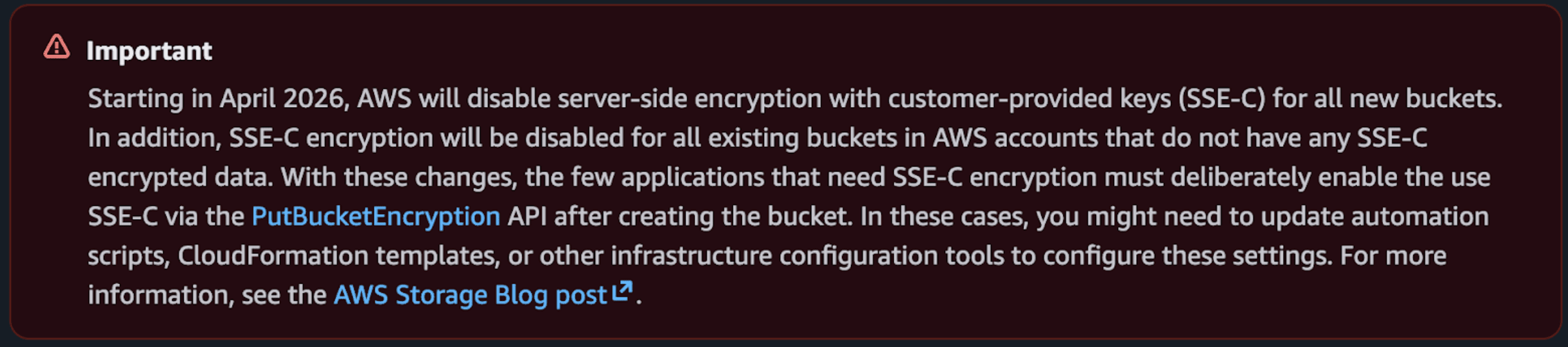
AWS has deprecated S3 SSE-C encryption, and in April AWS will disable the ability to use S3 SSE-C (Server-Side Encryption using Customer-Managed Keys). Below are steps to query Amazon S3 and confirm whether any objects use SSE-C encryption, along with steps to prevent SSE-C usage and recommended alternative solutions.
Here is the official announcement from Amazon:
What is AWS S3 SSE-C Encryption?
SSE-C introduced the first implementation of customer managed encryption in AWS S3, and it predates AWS KMS (Key Management Service) with CMK (Customer-Managed Keys aka KMS Keys).
With SSE-C, AWS required S3 Pu/Get API calls to include the key. AWS would encrypt/decrypt on upload/download, and then immediately discard the key.
The responsibility for the management of the key and mapping of which key was used for which object fell to end users. In practice this was cumbersome and risky, and it also means if you lose the encryption key, you lose the object.
For full details, here is the AWS S3 SSE-C User Guide: https://docs.aws.amazon.com/AmazonS3/latest/dev/ServerSideEncryptionCustomerKeys.html
Ransomware Concern
It turns out, this was pretty effective for abuse by ransomware. In 2025 an attacker used compromised AWS keys to encrypt S3 bucket data via SSE-C, and I suspect this attack prompted its deprecation by AWS, to prevent similar attacks in the future.
Ransomware Attack Narrative from Halcyon:
https://www.halcyon.ai/blog/abusing-aws-native-services-ransomware-encrypting-s3-buckets-with-sse-c
How to determine if AWS S3 SSE-C Encryption is in use in your AWS Environment?
All S3 objects have metadata, and in this metadata is a value for Encryption Type. Specifically, the values needed to determine if SSE-C is in use are ServerSideEncryption and SSECustomerAlgorithm. There are several ways to check the metadata for S3 objects, and the best tool for the job depends on the number of objects you need to check.
For a small number of objects, it would be feasible to run cli commands for each object. A shell or python script can quickly check a larger number of objects.
Using the s3api cli, the get-object would return the object and its metadata, but that is not necessary. The “head-object” command will return only the metadata for an object.
https://docs.aws.amazon.com/cli/latest/reference/s3api/head-object.html
Another option is to create an S3 Inventory. Amazon S3 Inventory provides a flat file list of your objects and metadata about the objects (including encryption type). Depending on your security reporting needs, this might be a good feature to set up for future compliance reporting.
The first step is to create a new bucket for the inventory files. After the bucket is created, configure the inventory to be updated on a recurring schedule.
Example cli command to create an S3 Inventory:
aws s3api put-bucket-inventory-configuration \
--bucket amzn-s3-demo-bucket \
--id 1 \
--inventory-configuration '{"Destination": { "S3BucketDestination": { "AccountId": "123456789012", "Bucket": "arn:aws:s3:::amzn-s3-demo-bucket", "Format": "ORC" }}, "IsEnabled": true, "Id": "1", "IncludedObjectVersions": "Current", "Schedule": { "Frequency": "Weekly" }}'
AWS S3 Inventory User Guide: https://docs.aws.amazon.com/AmazonS3/latest/userguide/configure-inventory.html
Once the inventory contains data, Athena can query the inventory and filter on encryption status (SSE-C).
Example Athena Query for SSE-C:
SELECT
bucket,
key,
version_id,
size,
last_modified_date,
encryption_status
FROM
<inventory bucket table name>
WHERE
encryption_status = 'SSE-C'
AND dt = '<most recent inventory report date>'
These steps, as well as additional details are in this AWS RePost:
Note: this article also includes a solution for consolidating S3 inventories Org-wide via multiple accounts and regions, so that they can be queried at scale.
If you have difficulty determining the source of the SSE-C encrypted objects, you can configure AWS CloudTrail to log these events. By default CloudTrail doesn’t log data events, and as you likely would expect, additional charges apply for logging these additional events.
AWS CloudTrail S3 Data Logging Guide:
What can you do now?
If SSE-C is in use, take the following steps to migrate away from AWS S3 SSE-C encryption.
- The first step is always discovery. Figure out who is using SSE-C, and why.
- Develop a plan for refactoring the workload to use one of the alternatives listed below.
- Implementing logging and alerting on SSE-C Usage (via CloudTrail).
- Implement one of the alternative solutions listed below.
- Restrict SSE-C usage via resource policy applied to an S3 bucket, or by a resource control policy (RCP) applied to an organization.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "RestrictSSECObjectUploads",
"Effect": "Deny",
"Principal": "*",
"Action": "s3:PutObject",
"Resource": "*",
"Condition": {
"Null": {
"s3:x-amz-server-side-encryption-customer-algorithm": "false"
}
}
}
]
}
What should you be using instead of AWS S3 SSE-C Encryption?
AWS recommends KMS (Key Management Service) for most use cases
- This is the most common solution, and it meets most compliance and regulatory requirements.
- KMS supports auditing, access controls, rotation, and lifecycle management.
- KMS CMKs allows key material to be imported for full key control.
Client-Side Encryption (For Maximum Isolation)
- Encrypt data before uploading it to S3
- Encryption keys never leave the customer’s environment
- Ideal for highly sensitive data requiring strict separation from cloud providers
Triaxiom Security: Comprehensive, Actionable, Results-Driven Security
Don’t let hidden vulnerabilities put your business at risk. Our comprehensive cloud security risk assessments provide the visibility and actionable insights you need to protect your organization from evolving cyber threats.
When you partner with Triaxiom Security, you’re not just getting a security assessment – you’re gaining a strategic advantage:
- Certified cloud security experts with deep expertise across all major cloud platforms
- Proven methodology refined through hundreds of successful security assessments
- Actionable recommendations prioritized by business impact and feasibility
Our expertise spans across all major cloud platforms and security domains. Whether you’re planning a cloud migration (see our considerations for moving to the cloud), need comprehensive AWS security assessments (learn what to expect from our AWS security assessment process), or require specialized penetration testing in cloud environments (explore our cloud penetration testing services), we have the expertise to protect your organization.