AWS CodeBreach: A Close Call For All
Yesterday (1/15/2026), Wiz published research detailing a vulnerability they named CodeBreach, and to say it was a close call is putting it mildly.
This may sound dramatic, but this had the potential to be devastating. This vulnerability struck at the system that distributes code to the AWS Console itself, and if it had fallen into the wrong hands, attackers could have used this to gain access to millions of AWS accounts.
We can learn valuable lessons from this research, and special thanks should be given to these security researchers.
Blast Radius – Big and Bad
I really do hate to sound dramatic, as I pride myself on being the calm voice in times of turbulence. Its hard to fathom what the impact of this could have been.
A large-scale AWS credential compromise such as this would have been a systemic event with major economic and societal impact. Businesses, healthcare systems, financial services, governments, and critical infrastructure all depend on AWS. A failure at that scale would be felt far beyond AWS itself. AWS itself is a 3 Trillion dollar company, but the AWS cloud infrastructure hosts many of the world’s most valuable digital companies, making its real economic value far beyond just its own revenue.
A few months ago AWS had a brief partial service degradation (dynamo) and it caused ripples across applications and software services across the globe.
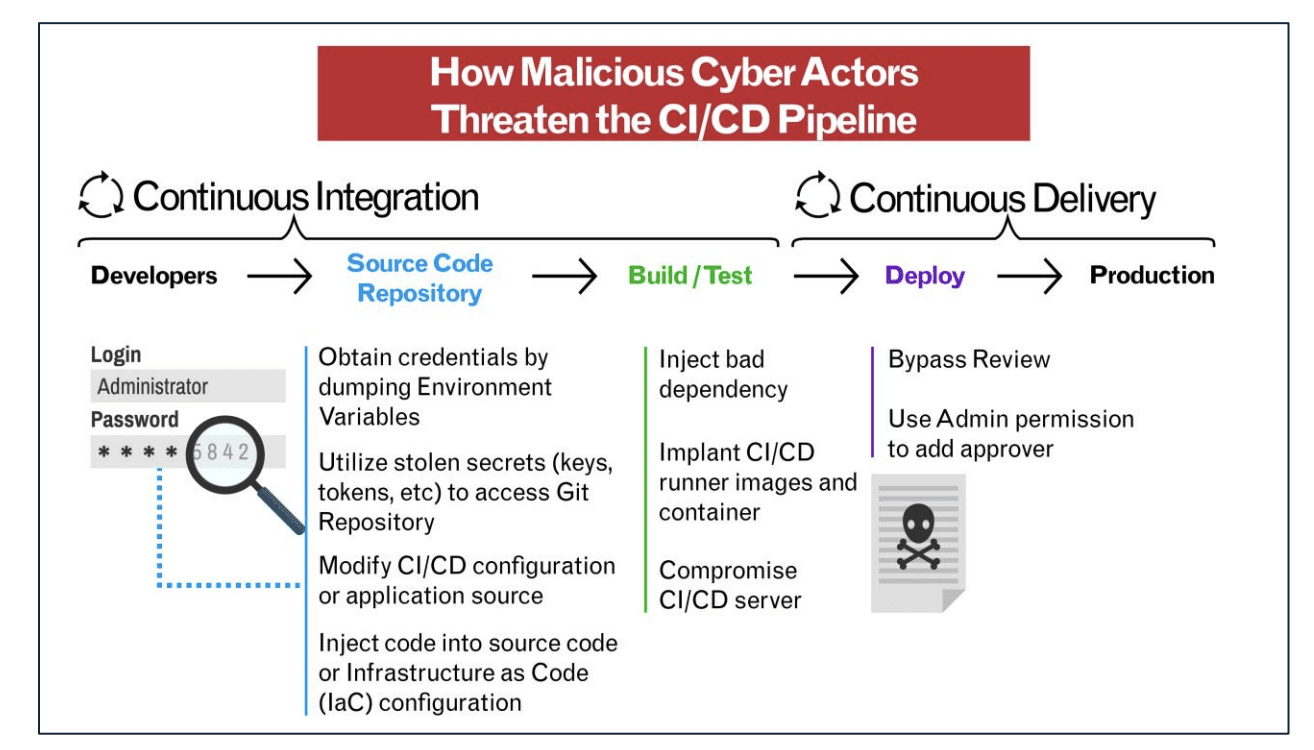
What Happened – CICD (supply chain) Vulnerability
This textbook example of why adversaries focus on CI/CD systems. These build and deployment pipelines are high-trust systems, and a small weakness can enable the injection of malicious code. This is far more impactful than attacking published applications because compromising a pipeline can give an attacker leverage over everything that can be produced by the pipeline.
In short, the vulnerability was to the CI/CD pipeline that deployed code to a core javascript SDK that is used by the AWS Console. They could have injected code into the AWS Console that could have harvested credentials from all AWS Console users.
Security Lessons – TODOs and Takeaways
This type of vulnerability shows the complexity and difficulty in securing CI/CD pipelines (supply chain).
The key security lessons here are clear:
- Reduce CI/CD pipeline privileges wherever possible
- Implement strict build and approval gates
- Ensure untrusted contributions can never trigger privileged pipelines
- Treat CI/CD systems as high-value targets, not just developer tooling
For security practitioners, here are the AWS documents for setting this up securely:
- https://docs.aws.amazon.com/codebuild/latest/userguide/pull-request-build-policy.html
- https://docs.aws.amazon.com/codebuild/latest/userguide/webhooks.html
- https://docs.aws.amazon.com/codebuild/latest/userguide/connections-github-app.html
The NSA and CISA provide the following recommendations and best practices for improving defenses in cloud implementations of development, security, and operations (DevSecOps):
https://media.defense.gov/2023/Jun/28/2003249466/-1/-1/0/CSI_DEFENDING_CI_CD_ENVIRONMENTS.PDF
Stewardship – White Hat Appreciation Day
We owe some gratitude to ethical security researchers, especially the research team at Wiz.
Ethical research and responsible disclosure enables the industry to understand these vulnerabilities and address their own risks before the they can become a reality. Knowing about issues like CodeBreach isn’t just interesting, it’s an excellent learning opportunity for anyone responsible for securing modern cloud environments.
Ethical security researchers are protecting our companies, economies, and enabling the broader security community to learn and adapt.
As AWS stated in their response:
“We would like to thank Wiz’s research team for their work in identifying this issue and their responsible collaboration with us to ensure that our customers remain protected and secure.”
That collaboration is a great example of collaboration in cloud security is supposed to work.
Here is the security advisory published by AWS:
https://aws.amazon.com/security/security-bulletins/2026-002-AWS
If you want to dig into the details of the attack:
https://www.wiz.io/blog/wiz-research-codebreach-vulnerability-aws-codebuild
Triaxiom Security: Comprehensive, Actionable, Results-Driven Security
Don’t let hidden vulnerabilities put your business at risk. Our comprehensive cloud security risk assessments provide the visibility and actionable insights you need to protect your organization from evolving cyber threats.
When you partner with Triaxiom Security, you’re not just getting a security assessment – you’re gaining a strategic advantage:
- Certified cloud security experts with deep expertise across all major cloud platforms
- Proven methodology refined through hundreds of successful security assessments
- Actionable recommendations prioritized by business impact and feasibility
Our expertise spans across all major cloud platforms and security domains. Whether you’re planning a cloud migration (see our considerations for moving to the cloud), need comprehensive AWS security assessments (learn what to expect from our AWS security assessment process), or require specialized penetration testing in cloud environments (explore our cloud penetration testing services), we have the expertise to protect your organization.
Final Thoughts
Ready to strengthen your AWS environment? Whether you are preparing for compliance, addressing a recent misconfiguration concern, or proactively managing risk, our team is here to support you. We will give you a clear view of your current cloud security posture and provide a practical roadmap to enhance it.
Continue reading to learn about common security gaps in AWS.
Schedule a free introduction call and learn how we can help you get confidence in your cloud security.